From One Click to Chaos: The Data Breach That Threatened Us
I used to think data breaches only affected big institutions.
Banks. Tech firms. Governments.
Not everyday people.
Not Leo volunteers like you and me.
Not clubs like ours.
We weren’t worth targeting… or so I thought.
But in earlier this month (June 2025), reality caught up to me.
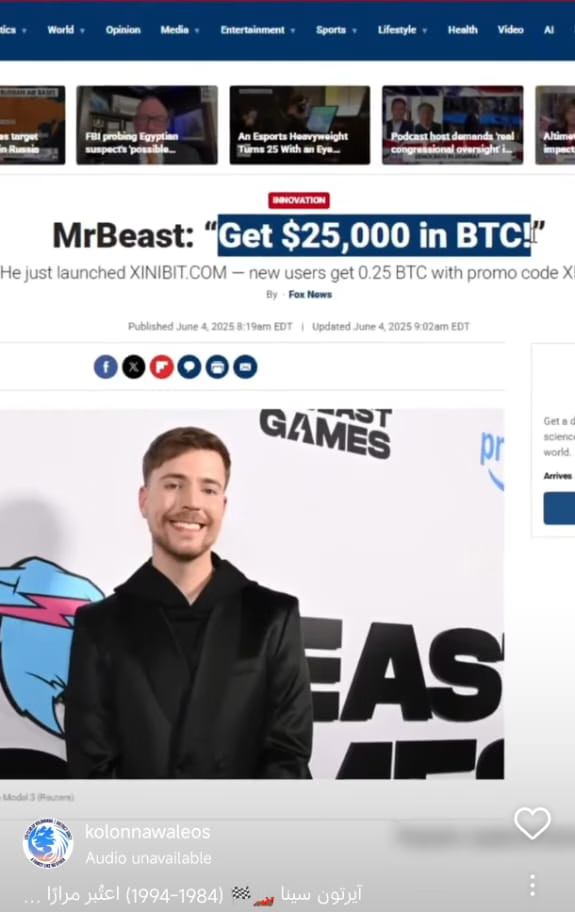
It started with a strange post on our Leo Club’s Instagram — some crypto spam I hadn’t seen before. My first reaction? Maybe someone else on the team had clicked a bad link. It happens, right?
But then things escalated.
When It Hit Me: I Was the One Breached
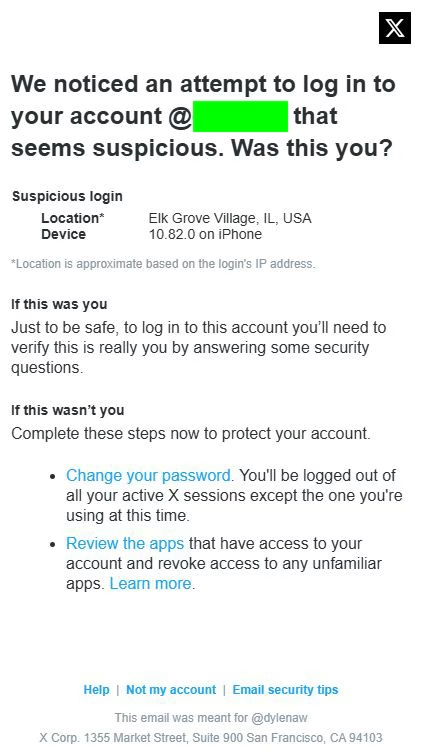
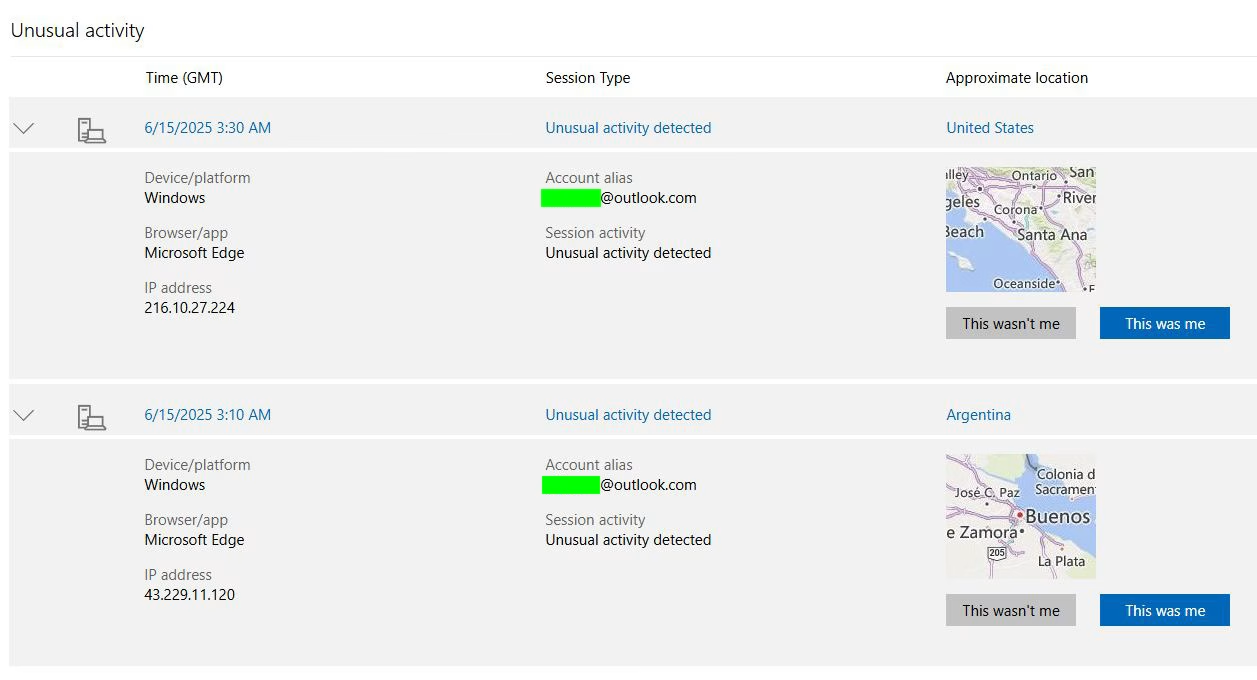
Soon, I was flooded with alerts.
Login attempts from the USA, Thailand, Canada, Nigeria, Taiwan.
Emails I never sent. Password resets I never requested.
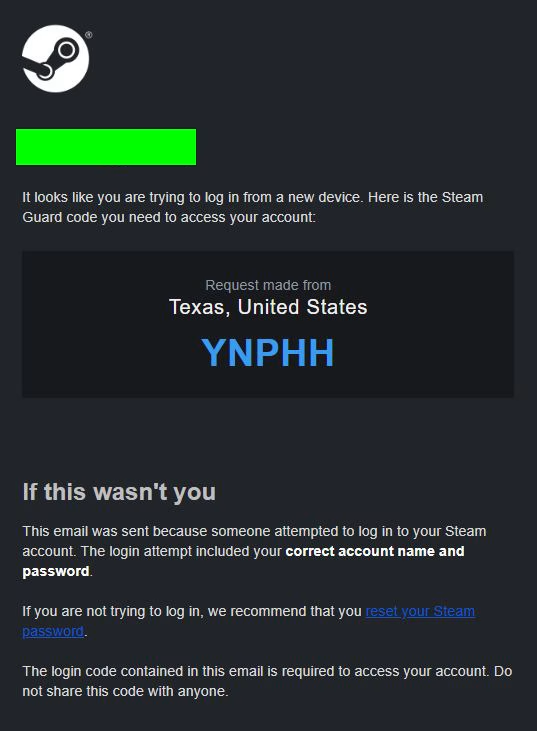
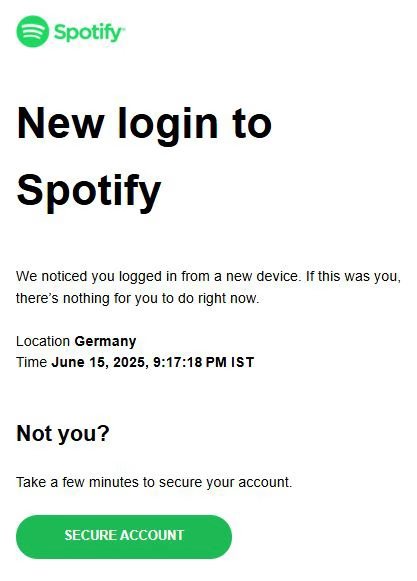
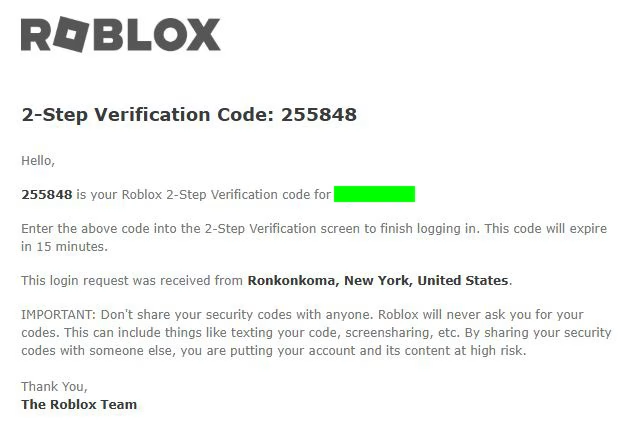
Instagram. Gmail. Facebook. Reddit. Steam.
Every platform I used… compromised.
It wasn’t someone else’s mistake.
It was mine.
How I Got Infected — And Didn’t Know It
Looking back, the breach began about a month earlier. I had downloaded a tool I thought was safe — Windows Defender flagged it, but I figured it was a false alarm. So I disabled protection and ran it.
Nothing happened, or so I thought. I got cautious, formatted my PC, and assumed I was clean.
But what I didn’t know was that the damage had already been done.
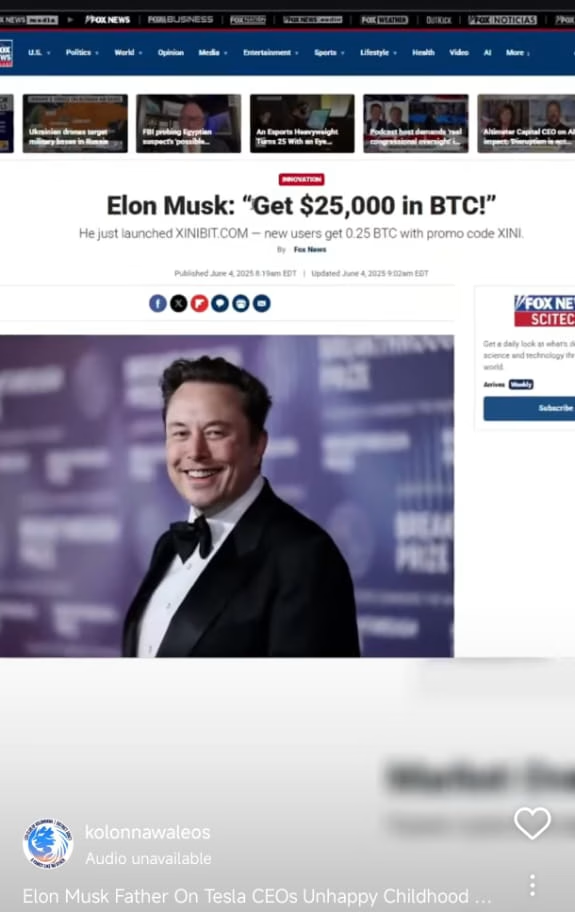
The tool I ran? It was infostealer malware, likely from the Lumma Stealer family — one of the most active strains of 2025. Before I formatted the PC, it quietly extracted every saved credential in my browser.
That included:
- Leo Club Gmail
- Instagram admin login
- Our website backend
I had handed over the keys without even realizing it.
The Bigger Picture: May 2025 Password Leak
As I tried to piece together the breach, I stumbled across a ZDNet article.
It detailed a massive plaintext password leak discovered in May 2025 — 47GB of stolen credentials from around the world.
No encryption. No password protection. Just millions of usernames and passwords out in the open.
And I was in there.
Security experts linked it to malware families like Lumma Stealer — tools designed to exploit people like me: regular users who store passwords in browsers, autofill credit card data, and have admin access to pages that matter.
That’s when it hit me:
This wasn’t a random hack.
This is how passwords get leaked — and it’s happening at scale.
What Saved Us (Barely)
Luckily, we had a few precautions in place:
- Recovery emails and backup phone numbers
- 2FA on a few key accounts
- A responsive team that flagged suspicious activity early
That helped us avoid total loss. But it was close.
What I Did After the Cyberattack
Here’s how I responded — and what I hope others will do before it’s too late:
🔍 Full Malware Cleanup
Even after formatting, I scanned again using Malwarebytes and Windows Defender. Cleaned up leftover traces and ensured no backdoors remained.
🔐 Reset Every Password
All personal and club accounts got a fresh start. New passwords. No duplicates. No reusing anything.
📦 Moved to a Password Manager
I stopped using browsers to save credentials — those files can be accessed by malware in seconds. I now use a trusted password vault.
🛡️ Enabled 2FA Everywhere
Every account that matters — especially those tied to our club — now has two-factor authentication.
🔎 Monitored Sessions and Devices
I logged out of everything, reviewed device history, and purged suspicious sessions.
🔁 Began Regular Security Reviews
Tools like HaveIBeenPwned and Google’s Password Checkup are now part of my monthly digital hygiene.
Why Leo Clubs Need Cyber Awareness
We often focus on leadership, service, and outreach. But we forget that in today’s world, digital responsibility is leadership.
If one volunteer’s device gets compromised, the consequences can ripple outward:
- Public event pages defaced
- Club email hijacked
- Volunteer data stolen
- Website security breached
That nearly happened to us.
Because that volunteer… was me.
What You Can Do Right Now
- Never ignore or disable antivirus — even briefly
- Don’t store passwords in browsers
- Use two-factor authentication on everything
- Talk to your club members about cyber safety
- Audit your shared accounts and reset old credentials
The Wake-Up Call I Didn’t Want — But Needed
That week was a blur of panic and regret.
Every morning brought new alerts: failed logins from places I’d never been.
It was exhausting.
It was scary.
But it was also a lesson I’ll never forget.
And now that we’ve rebuilt our defenses, I want others to learn from it.
Because whether you’re managing a club page, sending out event invites, or just logging in to a shared Google Drive — you are a gatekeeper.
We can’t afford to treat cybersecurity like an afterthought.
Not anymore.